Everything you need to
automate Hacking
The ultimate platform that combines CI/CD-like automation, project management, and advanced tooling for modern bug bounty hunters.
Manage projects
Organize your targets, and re-use your workflow templates to quickly start hacking on a new target.
CI/CD like workflows
Automate scans by creating workflows, and re-use it across targets.
Self-hosted Runners
Host runners on your own infrastructure, and run any command you want. Even your proprietary ones.
Bhlast servers
Burp collaborator like server, listen on incoming requests and respond to them.
Payload management
Store common payloads and re-use them across targets simply by changing the variable.
Notifications
Get notified on scan findings, or when a request is made to your bhlast server.
Automation is a solved problem
CI/CD systems have been around for a while now. They automated manual tasks. So why not automate the hacking process with the same principles, and expand it to include other hacking tasks like listener servers (like burp collaborator), payload management, notifications, etc?

Passionate about combining automation with security research to empower the bug bounty community
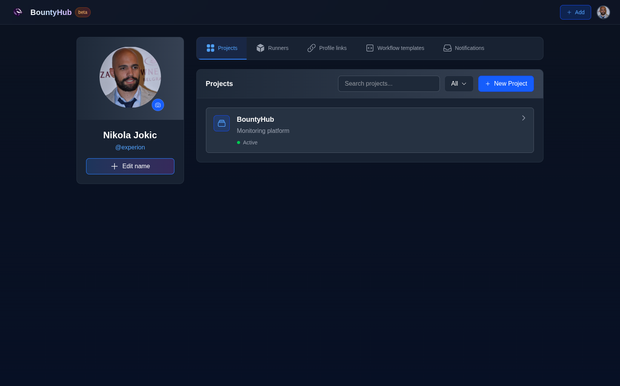
Manage multiple active/inactive projects
Each project is usually your target, but it doesn't have to be. Organize them as you see fit. When you stop hacking on one of them, you can simply deactivate it and activate it again when you want to hack on it again.
Gradually build your workflow
When you see yourself repeating the same steps over and over again, you can improve your existing workflow by adding steps/scans to it. Previous versions will be kept, so you can always go back or inspect the results.
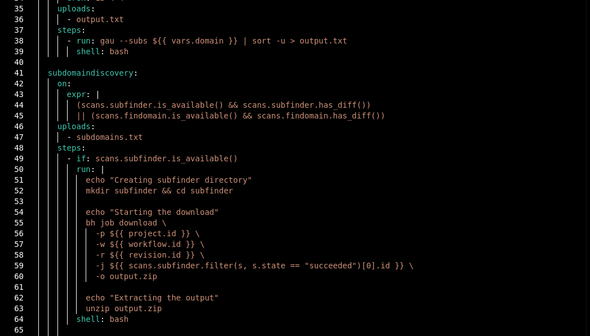

Host runners on your own infrastructure
Register runners on your machines. Running on your own infrastructure gives you power to install any tools you want, and run any command you want. You can have your proprietary tools installed and use them seamlessly.
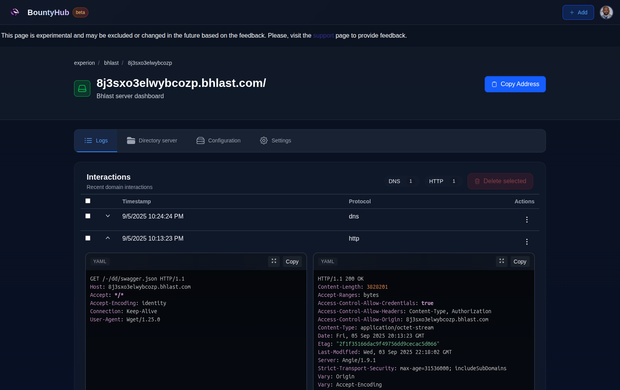
Listen for interactions
Get notified when blind payloads fire, and respond to them in real-time. Register custom DNS records and serve exploits from a single server provisioned with one click.
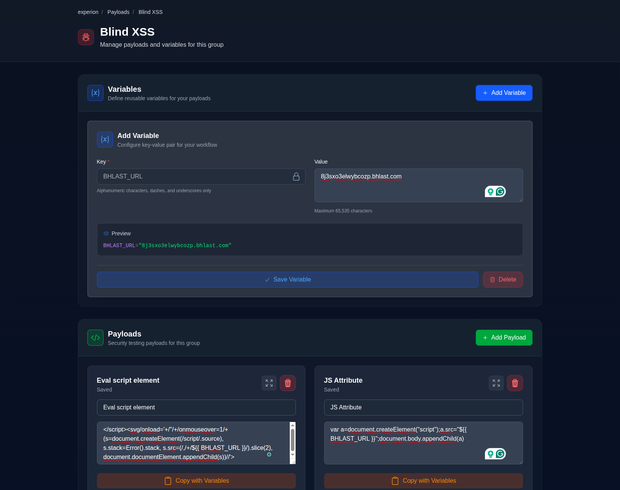
Manage payloads and template them for reuse
Store your payloads in the platform, and use them across your projects. Template your payloads so tailoring them to your target is a breeze.
Ready to Transform Your Hunting?
Join the revolution of automated bug bounty hunting. Start building your workflows today.